A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library

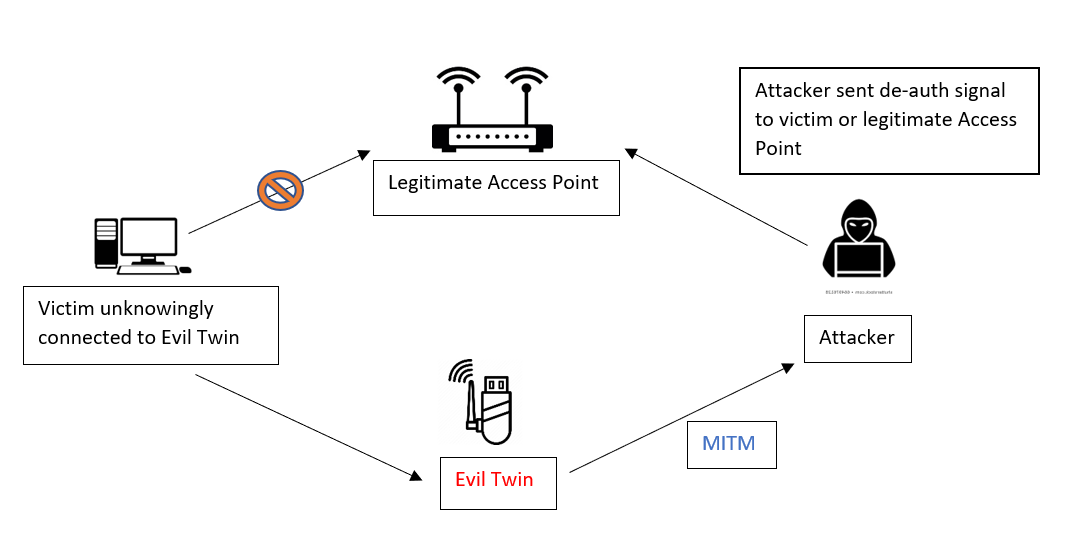
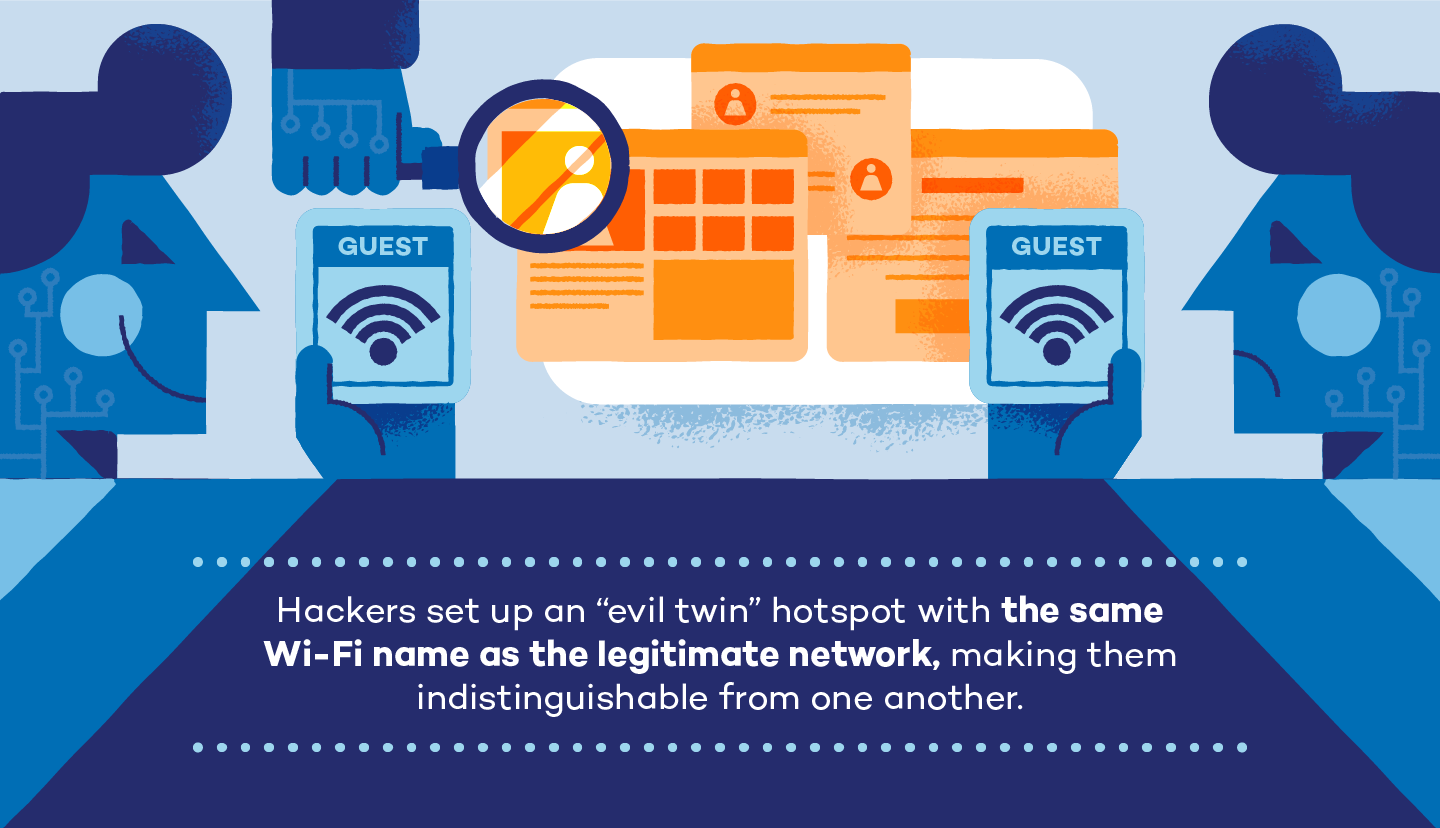
Don't fall victim to an evil twin attack. Here's how you can protect yourself - Siccura - Private and Secure Digital Life

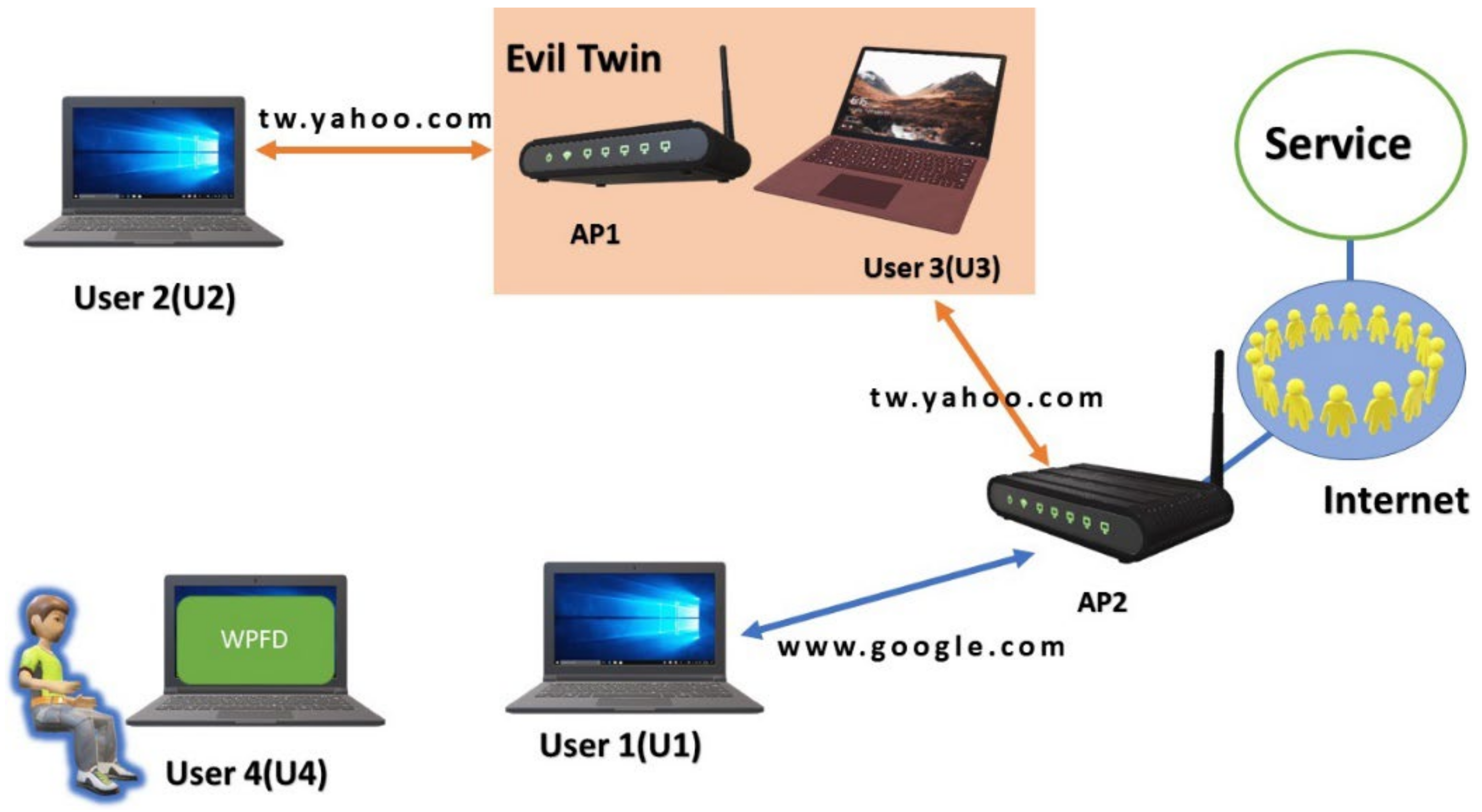
A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library
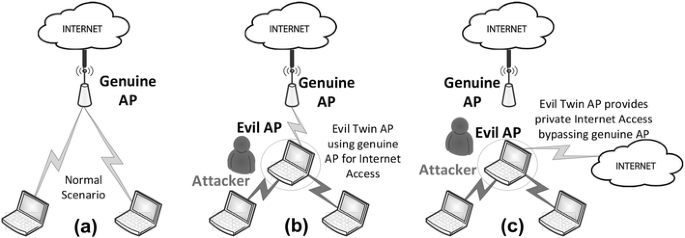

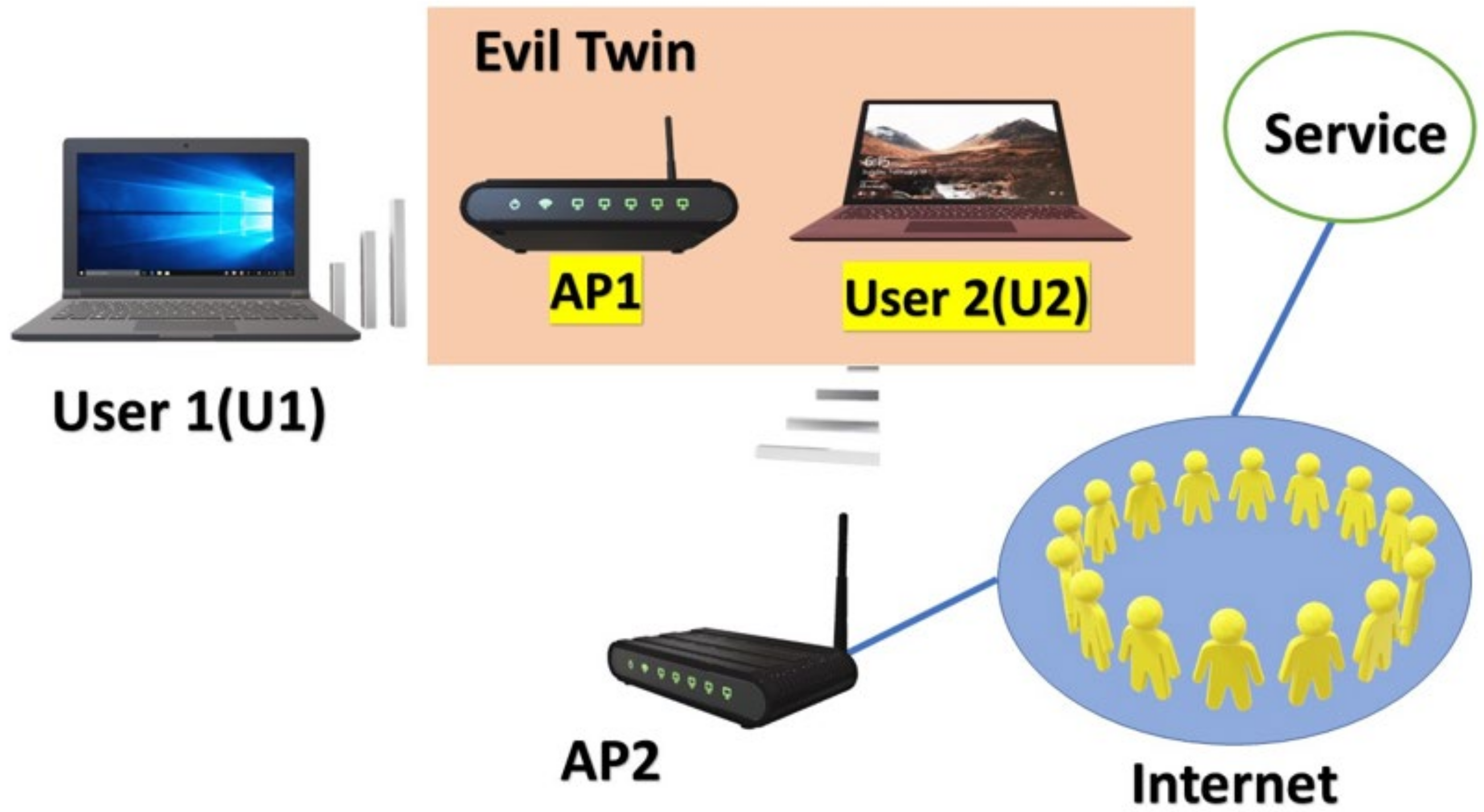





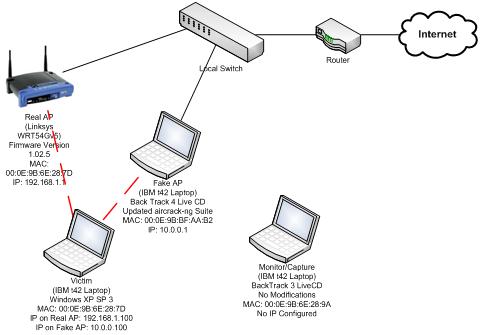
![PDF] Evil Twin Attack Mitigation Techniques in 802.11 Networks | Semantic Scholar PDF] Evil Twin Attack Mitigation Techniques in 802.11 Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c7f8f05a26716f23022a0a028a628962a1a06612/2-Figure1-1.png)